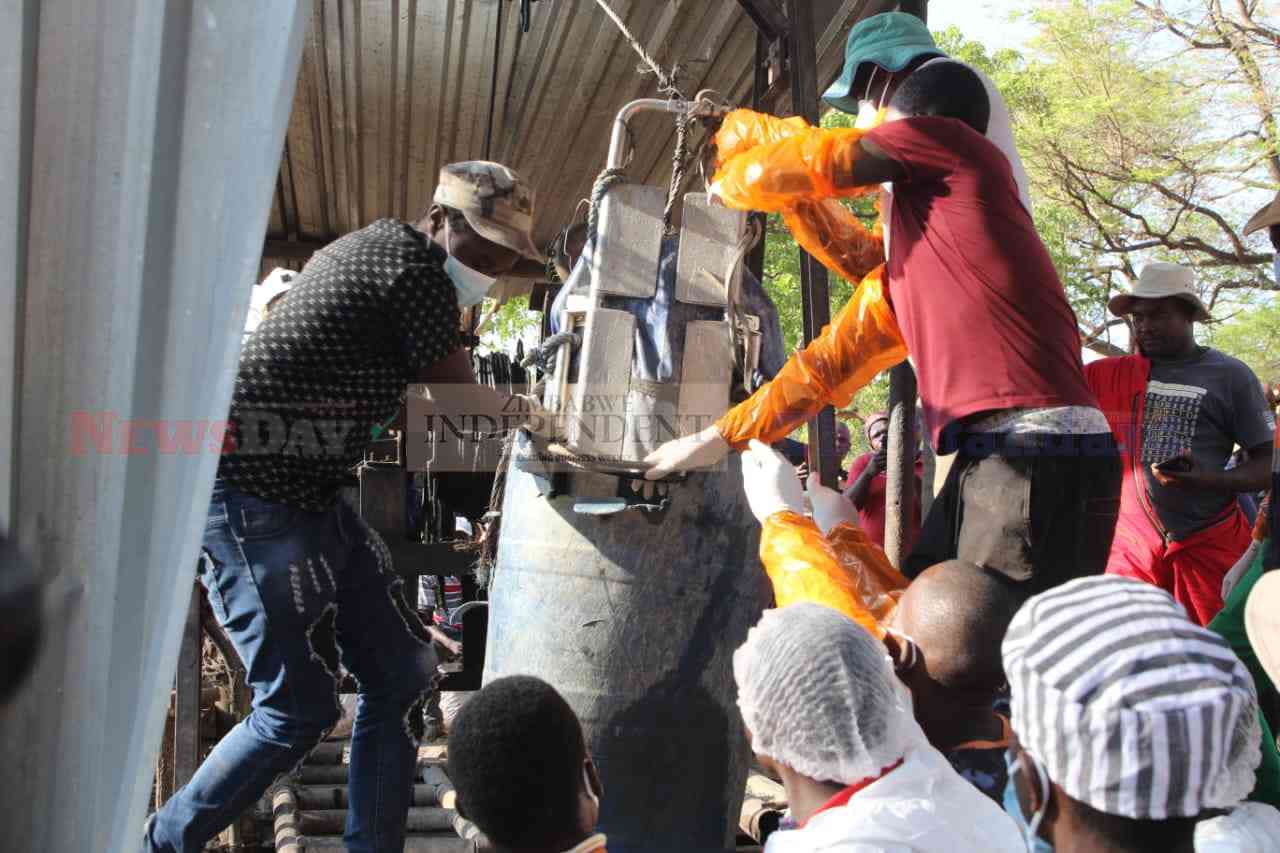Mushshak is an Urdu (official Pakistan national language) word which translates to proficient.
Premium
Zim mulls categorising black market as money laundering

Several suspected illegal foreign currency traders were arrested in Harare’s central business district this week.
By Tafadzwa Mhlanga
12h ago
Premium
Zim secures multi-million dollar jet deal
Mushshak is an Urdu (official Pakistan national language) word which translates to proficient.
By Tinashe Kairiza
12h ago
Rest, good sleep contribute to better health, happiness
By Admin
Feb. 17, 2023
Everyone eligible is encouraged to donate blood, help save lives
By The Independent
Jun. 10, 2022
ICT minister lauds Econet’s stand at the ZITF
By Donald Nyandoro
Apr. 25, 2024
Hope for lifting ban on OM, PPC chips
By The Independent
Aug. 26, 2022
Without planes, AirZim board won’t perform wonders
By The Independent
Aug. 5, 2022
Power crisis needs urgent attention
By The Independent
Jul. 29, 2022
Don’t print cash for projects
By The Independent
Jul. 22, 2022
Exploring the vibrant world of sports betting in Ethiopia
While the allure of sports betting is undeniable, it's crucial to approach it with caution and responsibility.
By Theindependent
Mar. 11, 2024
Satewave churns out power solutions for Zim
Satewave Technologies director Xiao Feng said the company has several solar solutions to address the current power challenges.
By Staff Writer
Aug. 15, 2023
Liquid Tech to increase tariffs by 50%
By Staff Writer
Mar. 31, 2023
Jotter: Students develop an integrated learning app
By Staff Writer
Mar. 17, 2023
Innovative crowd-investing app ‘PiggyBankAdvisor’ launched
By Staff Writer
Mar. 17, 2023
Meta gives up on NFTs for Facebook and Instagram
By The Verge
Mar. 15, 2023
Reasons To Buy Bitcoin From A Trading Platform
Another fundamental reason behind getting the coins from this particular space is that it provides
By Theindependent
Mar. 2, 2023
Why do banks not want people to rely upon cryptocurrencies?
Cryptocurrency transaction volume is much less than the fiat currencies, leading to a lack of liquidity in the market.
By Theindependent
Feb. 9, 2023
Premium
Zim football is 200 years behind: Chunga

Chunga was speaking during the Chunga Academy week-long holiday coaching programme at Zimbabwe Grounds in Highfield, Harare.
By Sports Reporter
14h ago
International day of jazz: Local concert on the cards
By Khumbulani Muleya
Apr. 19, 2024
Book Review: African decolonisation in Southern Rhodesian Politics, 1950–1963

The book begins by examining how white Rhodesians sought to push-back, delay or prevent African nationalism
By Anotida Chikumbu
Apr. 12, 2024
Moozy captivates audience at homecoming showcase
By Khumbulani Muleya
Apr. 12, 2024
Women take over the stage at Sofar
By Staff Writer
Mar. 28, 2024
Herbicides: Bad news for local food security
By The Independent
May. 27, 2022
Dumpsite: Gweru feels the heat
By The Independent
May. 13, 2022
Zim to pay 100% of international hunting revenue to communities
By The Independent
Jun. 10, 2022
.
Videos
Pamela Marwisa In Conversation With Trevor
By The NewsDay
Feb. 28, 2024
Job Sikhala, Zimbabwean Opposition Politician In Conversation With Trevor
By The NewsDay
Feb. 28, 2024
ExtremeWeather: Parts of Harare experienced flash floods on Sunday
By The NewsDay
Dec. 21, 2023
Harare motorists negotiate the city’s treacherous roads
By The NewsDay
Dec. 21, 2023
Solomon Guramatunhu Day 1
By The NewsDay
Dec. 14, 2023
Sengezo Tshabangu - In Conversation With Trevor
By The NewsDay
Dec. 5, 2023
Welcome to Alpha Media Holdings Zimbabwe - NewsDay - The Standard - The Zim Independent
By The NewsDay
Dec. 5, 2023
Dock sheep tail to maintain weight

The most common way of docking tails is by using an elastic and expandable latex ring. The rubber ring is expanded with an elastrator and put over the tail, where it is released.
By Kudakwashe Gwabanayi
Mar. 22, 2024
Asparagus worth your while (II)
By Kudakwashe Gwabanayi
Mar. 1, 2024
Why it makes sense to farm meat goats
By Shane Brody
Jul. 7, 2023
How to start a fish farming business
By Kudakwashe Gwabanayi
May. 26, 2023
Climate change is real, be alert
By Kudakwashe Gwabanayi
May. 12, 2023
Winky D promises to shutdown Bulawayo
The Vigilance Band and I are prepped to bring the fire. It'll be a night to remember, so don't miss out!"
By Sindiso Dube
8h ago
Prophet lauds Tanzania, Zimbabwe relationship
Madzibaba Jonah usually goes around the continent and Asian countries where he joins other apostolic members in prayer.
By Style Reporter
Apr. 25, 2024
Wash boost for indigenous churches
By Style Reporter
Apr. 24, 2024
Mahachi pays tribute to late SA gospel icon
By Style Reporter
Apr. 23, 2024
Richest Forex Traders in Tanzania
By The Standard
Apr. 22, 2024
Govt gifts Byo with textile manufacturing firm
“The project also aims at contributing to the reduction of gender-based violence, youth unemployment and gender inequality, and addressing shortage of skills, among women and youths.”
By Daniel Moyo
19h ago
Gwanda water crisis deepens
“Efforts to sink deeper the pipe that draws water are being made, but this is not a final solution, it's just a short term measure as we wait for Zinwa to bring water from Blanket Dam.”
By Silas Nkala
19h ago
We’ll be Zim’s industrial hub again: Coltart
By Silas Nkala
Apr. 25, 2024
Binga South MP, minister clash over boreholes
By Patricia Sibanda
Apr. 25, 2024
NDS1 failing to link govt, private sector: Cimas Boss

For the second year running Cimas Health Group is the platinum sponsor for the ZITF International Business Conference.
By Staff Reporter
6h ago