In the last 40 years, the term “cyber” has permeated headlines, conversations, and media discussions. The concepts of cyber warfare, cyber threats, and cybersecurity are frequently thrown around, but what is it about the word “cyber” that makes so many people roll their eyes?
What often elicits eye-rolls when the term “cyber” is invoked is its overuse and perceived sensationalism. News outlets tend to seize on the “cyber” angle of any online event, emphasising the drama and danger, often at the expense of critical context.
As a result, the public is bombarded with alarmist narratives, making it challenging to separate genuine threats from exaggerated claims.
This skepticism extends to the mislabeling of every cyber incident as a “war.” The blurring of lines between cyber skirmishes, hacktivism, espionage, and actual cyber-warfare has led to doubts about the terminology, which in turn, has led to doubts about the potency of the threat it represents. Is every instance of digital disruption truly a “war,” or do some merit a more nuanced assessment?
Let us explore real-life examples to separate hype from reality, examine why the term "cyber" provokes apathy and how we can discern the genuine threats in this complex, evolving landscape.
Cyber war hype
The term “cyber” has become ubiquitous, dominating discussions about national security, warfare, and global politics. It evokes images of shadowy hackers, high-stakes espionage, and invisible warfare fought on the internet’s virtual battlegrounds. However, as the use of “cyber” has proliferated, so has the skepticism surrounding its implications.
The skepticism surrounding "cyber" can be attributed to a variety of factors. One key reason is the blurred line between what constitutes a genuine cyber-war and what should be categorised as a skirmish, hacktivism, or cybercrime.
- Chamisa under fire over US$120K donation
- Mavhunga puts DeMbare into Chibuku quarterfinals
- Pension funds bet on Cabora Bassa oilfields
- Councils defy govt fire tender directive
Keep Reading
The media's tendency to label every cyber incident as a “war” dilutes the term’s gravitas. So how do we distinguish hype from reality in the realm of cyber warfare? What are the tangible consequences of these incidents, and when does a cyber-skirmish become a full-blown cyber war?
To answer these questions, we will examine two events – Estonia's 2007 cyberattacks and the 2010 Stuxnet incident – that shed light on what is really at stake in digital conflict.
Estonia's cyber skirmish
In April 2007, Estonia faced a massive wave of cyberattacks that disrupted government websites, news outlets, and financial institutions, following the relocation of a Soviet-era war memorial in Tallinn.
While these attacks garnered significant media attention and were labeled as a “cyber war,” some experts argued that they were more of a cyber-skirmish.
Estonia's cyber-attack is categorised as a skirmish because the attacks primarily involved online disruptions, were of a limited scale, and did not lead to extensive physical damage or human casualties.
The attacks primarily involved Distributed Denial of Service (DDoS) attacks, causing inconvenience, but not the widespread infrastructure damage associated with true warfare.
This incident highlighted the power of digital disruption but also raised questions about the validity of labeling every cyber incident as “war”. The attacks, while impactful, were relatively short-lived, lasting only a few weeks. The scale and scope of the attacks, while considerable, were largely confined to online operations.
While it is widely believed that the Russian government was behind the attacks, attribution was challenging, making it difficult to definitively categorise this as a full-fledged cyber war.
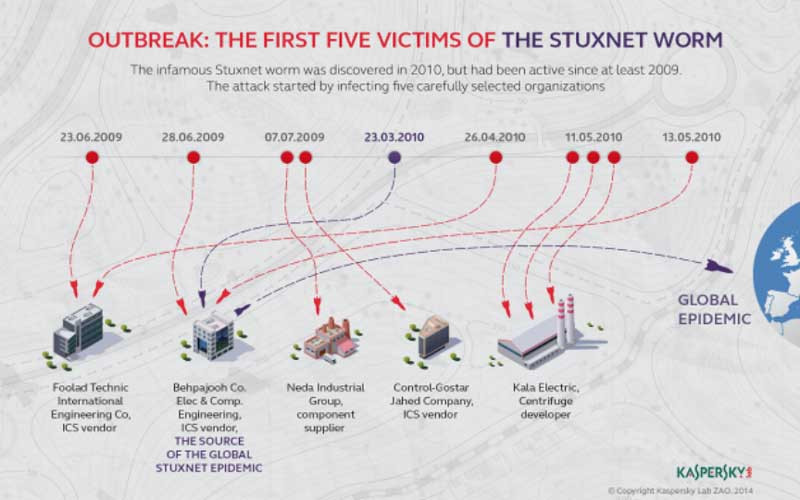
Stuxnet , the digital weapon
Stuxnet was a sophisticated computer worm that targeted Iran's nuclear program in 2010. It demonstrated a new era of cyber-warfare, as it was designed to damage specific industrial systems, ultimately causing physical harm.
Stuxnet's complexity and the fact that it was allegedly developed by nation-states blurred the line between cyber and conventional warfare. Stuxnet is a prime example of a cyber-physical attack, showing “cyber’s” deeper, kinetic nature.
Stuxnet was designed to infiltrate and damage specific industrial systems, particularly Iran's uranium enrichment centrifuges. The worm caused physical harm by making these centrifuges malfunction, disrupting critical infrastructure, which can be seen as an act of war.
Stuxnet was highly sophisticated and required a deep understanding of the targeted systems, suggesting the involvement of nation-states: in this case, the United States and Israel.
The sophistication and expertise involved in its creation and execution differentiates it from typical cyber skirmishes.
Stuxnet is closer to a cyber-war because it had a direct and significant physical impact, was highly sophisticated, had clear attribution, and generated lasting consequences.
Cyber security realities
In the digital age, where our lives are increasingly intertwined with technology, the term “cybersecurity” has become perceived as a beacon of protection against the malevolent forces that lurk in the virtual shadows.
While the concept of safeguarding our digital world is of utmost importance, it too is susceptible to the eye-rolling responses to the overuse of “cyber”.
The skepticism that sometimes greets discussions of cybersecurity may stem from a sense of overwhelming complexity.
The field is ever-evolving, with new threats emerging daily, each more sophisticated than the last, often demanding “zero day” patches and software updates when detected.
While the term "cybersecurity" encapsulates a broad spectrum of practices and tools dedicated to protecting our digital lives, it can feel broadly abstract, difficult to grasp and even harder to define.
It is critical to venture beyond buzzwords and consider the tangible impact of cyber threats, acknowledging that while they may not always escalate to full-scale “cyber wars,” have far-reaching consequences for individuals, organisations, societies, and governments. Putting hype aside, here are some of the threats we face today.
Ransomware attacks
Ransomware attacks, such as WannaCry and NotPetya, have crippled organisations worldwide, encrypting their data and demanding ransoms for decryption keys.
These incidents highlight the real and present danger of cyber threats. While not necessarily “war,” they highlight the extent to which cyberattacks can disrupt critical infrastructure, healthcare systems, and national security. Any skepticism about semantics should be set aside for a more thoughtful consideration of the threats.
Malware, phishing
Every day, innumerable malware variants and phishing schemes besiege the internet, constituting a continuous and pervasive menace. These threats may not make headlines like a high-profile “cyber-war”, but they pose a significant, sustained challenge to individuals and organisations alike.
The persistence of this onslaught often elicits the skepticism surrounding the term “cyber”, showcasing how the ubiquity of these attacks have lulled many into apathy… which sets the stage for exploitation.
Malware, a broad term for malicious software, takes various forms. It can be delivered through seemingly innocuous email attachments, malicious websites, or compromised software. Once it infiltrates a system, it can lead to data breaches, theft, or the takeover of computers and networks.
Phishing, on the other hand, relies on deception – social engineering – to trick individuals into divulging sensitive information, such as passwords and credit card details. These tactics are frequently used in combination with malware, amplifying the risks.
Individuals and organisations must maintain constant vigilance against these digital threats.
The battle against malware and phishing involves implementing and updating security software, education, and staying up-to-date with evolving threats.
Cybersecurity is not just about preparing for an abstract war; it is about actively countering threats that pose real and immediate risks to digital privacy and security.
The need to fend off these daily attacks serves as a stark reminder that the term “cyber” is not mere hyperbole but an ever-present and kinetic reality.
Attacks on critical infrastructure
Cyberattacks on critical infrastructure, such as power grids and water supply systems, pose a significant threat. While not all attacks are on the scale of Stuxnet, the potential for disruption remains. If such infrastructure is compromised, the consequences could be disastrous, with little defensive recourse but reaction and retaliation. This illustrates the tangible and substantial impact of cyberthreats.
The challenge of attribution
One of the factors that contribute to the skepticism surrounding cyber-warfare is the difficulty of attributing attacks to specific actors. In traditional warfare, it is relatively easy to identify the aggressor by their uniforms or insignia.
In this space, the lines are often blurred, and attackers can hide behind layers of anonymity. This has led to doubts about the legitimacy of some cyber-warfare claims.
Attribution challenges were vividly illustrated in the case of the WannaCry ransomware attack. While many experts believed it was the work of North Korea, it was challenging to provide definitive proof. This difficulty in attributing attacks to a specific source has led to doubts about the true origins and motives behind some cyber incidents, further contributing to skepticism.
Summary
The eye-rolling reaction to the term “cyber” is largely due to overuse and hyperbole in media and public discourse. The asymmetric consequences of these attacks, as seen in Stuxnet and other events, demonstrate the criticality of separating hyperbole from reality, recognising that not every cyber incident qualifies as a “war”.
So, while the skepticism is understandable, a sober assessment of the cybersecurity landscape remains critical. The cyber landscape is vast and complex, and understanding its nuances is the first step toward addressing the real challenges it presents.
- Ntambalika is a Zimbabwean-born researcher and strategist based between Zimbabwe, South Africa and the United States. His work focuses on the intersection of statecraft, strategy and security. He is a globally-recognised expert and thought leader on cyber security, intelligence, corruption and counter-terrorism, money-laundering and forensic accounting. — [email protected] or +27 64 919 3049 and +1 202 802 6391.